Smart home cybersecurity explained
At Minim, we take security seriously. Securing the Internet of Things (IoT) in people’s homes is our thing. But did you know it’s easy to take some big steps in the right direction on your own?
Being proactive about your security can make a world of a difference. Spending the time now to keep everything up-to-date can save time (and money!) down the road. Here’s our guide to securing your smart home’s network.
What is smart home cybersecurity?
Here’s the thing: most people don’t know that their connected home devices lack critical security updates that other devices—like laptops and mobile phones—regularly get.
Some smart devices lack system hardening (gives devices various means of protection to make them secure), and others might even have hardcoded passwords, or passwords that can be found without encryption, right inside the software of the device.
Security just isn’t a high priority for some connected device makers, and all it takes is one compromised device to allow hackers to access personal or sensitive data, leaving the entire home network at risk.
Here are a few scenarios of how your home could become compromised:
- A hacker gains access to your smart home thermostat, gaining the ability to know when you might be out of the house.
- A hacker gains access to a smart home speaker with listening capabilities, listening in to your conversations or accessing passwords and user data.
- Your smart device or entire network becomes compromised and is used to launch a DDoS attack against a remote device across the world.
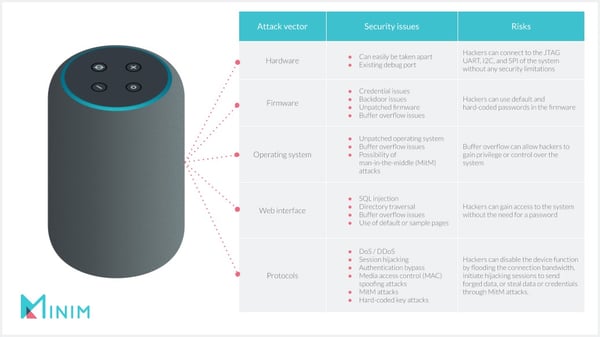
Common cybersecurity threats against smart home devices
There are dozens of types of attacks that smart home IoT devices can fall victim to. Just one device can have several attack vectors.
Here’s a run-down of the most common attacks IoT devices typically fall victim to:
Hijacking
Hijacking happens when hackers gain control of an IoT device. It’s difficult to know when this has happened as the device itself remains fundamentally unchanged. Device hijacking can be a real issue for home network security because, once one device has been compromised, the rest are sure to follow.
Data breach / identity theft
IoT devices gather lots of information about the end user. Personal information like addresses, phone numbers, health records (from wearables like smart watches) and even bank information is all handled by smart home devices. Hackers can target these devices and gain the information necessary to steal user identities.
Man-in-the-Middle (MITM)
Man-in-the-Middle attacks occur when a hacker interrupts or spoofs the communication happening between two devices. One MITM attack that made the news was when a Samsung smart fridge was compromised and allowed hackers to gain access to Gmail login credentials.
Distributed Denial of Service (DDoS)
A denial-of-service attack (DoS) is made to force websites, devices, or entire systems to shut down or become unavailable because of a disruption in its internet connection. DDoS attacks take DoS attacks one step further by flooding a targeted system or device with enough traffic to shut it down and stop it from working.
Often, hackers will gain control of IoT devices (usually without a user knowing) and harness the power of hundreds or even thousands of these compromised devices to launch DDoS attacks. The Mirai botnet attack is a big example of a massively distributed DDoS attack which left much of the eastern coast of the U.S. without internet.
Permanent Denial of Service (PDoS) / phlashing
Permanent denial-of-service attacks (PDoS) damage compromised devices to the point of replacement, often referred to as “bricking” a device. One example of a PDoS attack is a feed of inaccurate or faked data to a smart home thermostat that might cause extreme temperature fluctuations, resulting in physical damage to both the device and to the home.
Securing the smart home against cyber attacks
Now that you’re aware of the types of attacks that are most commonly seen affecting connected devices in the smart home, here are some tips on how to avoid them.
Change the name of your router
Your router’s default name can give insights that you don’t want to be made public. Hackers can use even small bits of information like a device’s name to infiltrate your network.
Use guest networks
Your WiFi, your rules. Keeping your WiFi access limited will ensure a lower likelihood of being compromised. Guests should only have access to a separate account that doesn’t leave your IoT devices exposed to a potentially compromised device.
Use WPA2 encryption on your router
Keep your router and traffic secure with WPA2 encryption. Other encryption methods might not be as strong—and never leave your network open without a password.
Disable unnecessary features
Many IoT devices will come with services like remote access, which is often enabled by default. Be sure to disable remote access authorization unless it’s being used, and make a point to go through the settings of your IoT devices to disable any other similar settings that you won’t be using. Minimizing these potential attack vectors will keep your devices safer.
Regularly update your devices
The security of your IoT devices is key. Check to see if your devices need to be updated on a regular basis. Otherwise, you might be missing out on critical security updates—and possibly some neat features, too.
Regularly update your router
The most common attack vector in the smart home is the router. For Minim customers and Minim-powered Motorola® systems like the MH7022, we ensure the router receives up-to-date firmware via our cloud; but if you do not have a cloud-managed router, you’ll want to check with your router manufacturer or ISP for updates. (If you have purchased or leased a router that doesn’t receive updates, consider a switch.)
Use unique passwords and 2FA
Using different passwords for each account or device ensures that, even if one account does become compromised, the others will still be safe. Enable 2 Factor Authentication (2FA) where possible to add that extra layer of protection to accounts. 2FA uses a second device, often a mobile phone or tablet, to send a code that will allow a user into their account. Most big social media companies have this feature available now, and it’s very likely big company accounts will too.
In conclusion
If you live in a home that has smart devices, you should be aware of the risks associated with them in order to better guard your personal data, privacy, and happiness. Smart devices can be tricky, but with the right management and know-how, they can also be rewarding.
To learn about how Minim can help you to better manage and protect your smart devices, visit our IoT security solutions page.