
Smart home cybersecurity news roundup [September 2019]
Smart home cybersecurity continues to be a hot topic as more vulnerabilities are found in consumer IoT. Vulnerable targets disclosed this month include millions of mobile phone models and several popular smart home routers.
Mobile phone vulnerabilities: SMS-based attacks
On September 12, 2019, researchers from AdaptiveMobile Security released their findings on Simjacker, an SMS-based attack that's been targeting nearly ever mobile phone in use for the past two years.
SIM cards are small replaceable chips that work as the mobile phone's identity to the cell provider, and are in essence small computers. The SMS-based attack described in the vulnerability disclosure works by bypassing a phone's OS and running the malware directly on the SIM. The malware running on the SIM card can then control the phone.
In the case of the Simjacker attack, the SMS message (aka Simjacker Attack Message) targets a certain software layer on the SIM card itself:
"This Simjacker Attack Message, sent from another handset, a GSM Modem or a SMS sending account connected to an A2P account, contains a series of SIM Toolkit (STK) instructions, and is specifically crafted to be passed on to the UICC/eUICC (SIM Card) within the device. In order for these instructions to work, the attack exploits the presence of a particular piece of software, called theS@T Browser- that is on the UICC. Once the Simjacker Attack Message is received by the UICC, it uses the S@T Browser library as an execution environment on the UICC, where it can trigger logic on the handset..."
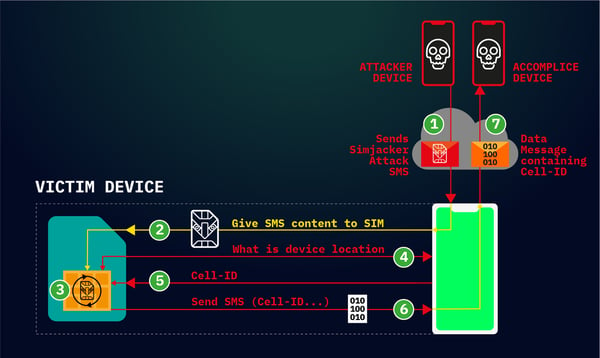
Simjacker attack flow (Source)
From what's shown in the Simjacker attack flow above, the attacker can pull location information from the device. In addition, instructions can also be executed to:
- Call a certain phone or send a short message
- Launch a browser that has more malware on it
- Pull more information (e.g., IMEI, Battery, Network, Language...)
- Disable the SIM card altogether, resulting in Denial of Service
The AdaptiveMobile Security researchers were able to observe the Simjacker attack successfully carried out across a wide range of device makes and models as the Simjacker attack method relies on the SIM card's software and not the physical device itself.
On a similar note to the Simjacker findings, another SIM-based attack was disclosed on September 21, 2019 by Ginno Security Lab. The researchers found a vulnerability in the Wireless Internet Browser (WIB), which is a SIM-browser or dynamic SIM toolkit.
Referred to as WIBattack, this SMS-based attack method can run a comparable set of commands that result in exposure of device information and execution of device activities like launch a browser, make a call, or send a message by sending an over-the-air (OTA) SMS to the victim's mobile phone.
To see just how these types of attacks are carried out, check out this WIBattack demo video:
Both AdaptiveMobile Security and Ginno Security Lab have also shared their findings with security experts, the SIMalliance, and also the GSMA, an organization which represents mobile operators.
Router vulnerabilities: Credential leaks and remotely exploitable bugs
On September 10, 2019, Security Researcher Simon Kenin from the Trustwave SpiderLabs security team disclosed 5 credential leaking vulnerabilities found in hardware by D-Link and Comba Telecom. Affected models include:
- D-Link DSL-2875AL
- D-Link DSL-2877AL
- Comba AC2400 Wi-Fi Access Controller
- Comba AP2600-I WiFi Access Point
The vulnerabilities found allow for passwords to be stored in clear text— unencrypted and easily retrievable by an attacker wishing to gain control of the router, and therefore, the home network.
In response to these findings, D-Link followed up and shared that they released security patches for the issues. Therefore, affected users will want to ensure their router firmware is up-to-date. Comba Telecom on the other hand has yet to acknowledge these findings at this time.

About a week later on September 16, 2019, researchers from Independent Security Evaluators released findings on more vulnerabilities in common small home and small office (SOHO) routers. As stated in their research, the 13 SOHO devices tested and found vulnerable included models by: Buffalo, Synology, TerraMaster, Zyxel, Drobo, Asustor, Seagate, QNAP, Lenovo, ASUS, Netgear, TOTOLINK, and Xiaomi.
"All 13 of the devices we evaluated had at least one web application vulnerability such as cross-site scripting (XSS), operating system command injection (OS CMDi), or SQL injection (SQLi) that could be leveraged by an attacker to get remote access to the device’s shell or gain access to the device’s administrative panel. We obtained root shells on 12 of the devices, allowing complete control over the device including 6 which can be remotely exploited without authentication: the Asustor AS-602T, Buffalo TeraStation TS5600D1206, TerraMaster F2-420, Drobo 5N2, Netgear Nighthawk R9000, and TOTOLINK A3002RU V1."
Their research highlights and discusses the specific vulnerabilities found in each device; it also states that each device manufacture was contacted with the findings either directly or through a bug bounty program. As can be seen in their disclosure details table, many of the manufacturers promptly responded while some have yet to acknowledge the findings.
Past smart home cybersecurity news roundup editions:
- June 2019: Linksys Smart WiFi router vulnerability and Android pre-installed backdoor
- July 2019: Website drive-by attacks on home routers
- August 2019: VxWorks and Google Nest Cam IQ Indoor vulnerabilities